
Email can truly be a delight to have and open to see what’s inside. It’s almost like opening a surprise gift. After all, email from friends, love interest, family or co-workers keeps us updated with whatever, is going on in that particular circle. Still, how do I know a legit or SPAM email?
Other times, there’s an email from a favorite #brand store usually to inform us about a sale or other information. How do we know if it’s a legit or SPAM email?
Fortunately for us, the majority of email programs will have anti-spam algorithms and filters which get ‘triggered‘ from certain features of SPAM emails, and get caught then tossed into our email Spam folder.
Types of SPAM Bots
Spam bots are created to infiltrate your computer and social media (SoMe) sites for different purposes. They will have coded instructions using first your computer, and then pass into your various connections online.

Coded Bots carry instructions for a variety of chosen actions to capture specific information ;
- copy your keystrokes to harvest your user names and passwords
- search your personal desktop or laptop for personal data to steal
- have you click on pay-per-click ads for their financial benefit
- use your computer as a Proxy so your internet connection hides their tracks, steal your bandwidth
- scan the web to scrape contact information
- use Phishing to steal account information especially in banking and shopping
- use email Spoofing to appear as a legitimate site
- spread malware through social media (SoMe) accounts
- spread malware through posts and comment threads
- lock out users to force ‘ransom’ payments
- use more than one spam bot
Purpose of using Spam
Criminals are predatory and will set up, and seek out a main goal. There exists a black market for stolen financial and personal data and it gets sold on the dark web. Lesson: Learn to change your Passwords, make them strong, and difficult. Record it in a pocket-size personal Telephone book. It’s offline.

Selling this information helps other criminals to set up a false credit card, steal and use your identity, and make fraudulent charges to your own account. They can even change your existing passwords and lock you out of your own accounts.

Your own financial information can also be captured from infiltrating legitimate business data processors. You know those news stories about big businesses reporting ‘data breaches‘? They will have enormous amounts of data that would demand higher prices when up for sale. Hence the reason for the term ‘ransom‘ ware payment demands.
Banking and personal information data helps criminals set up fake credit cards and using personal identification (birth, full names, home and mailing addresses, etc.), are used in identity theft.

Check out the Cyber Crime team
Luckily, we have Cyber security teams in government and our law enforcement agencies. They too are out there tracking and detecting these online criminals. Others are protecting data, or designing and launching security measures with installation, configuration and regularly updating security software. There’s teams that specialize in data breaches too. They must ALL stay up-to-date with technologies, coding and cyber security trends.
It appears that there’s a digital battleground going on around the world, and many are blissfully and totally unaware. We can take steps to help both ourselves and those #cyber security specialists too. We don’t have to be nor become victims.

Experience with a Spam email
Let’s examine the following image of a Spam email. As you can see. It practically SHOUTS at you about some great sale or other from what seems a ‘legit‘ store brand and then tells you to quickly click and get your offer or other ‘call to action‘.
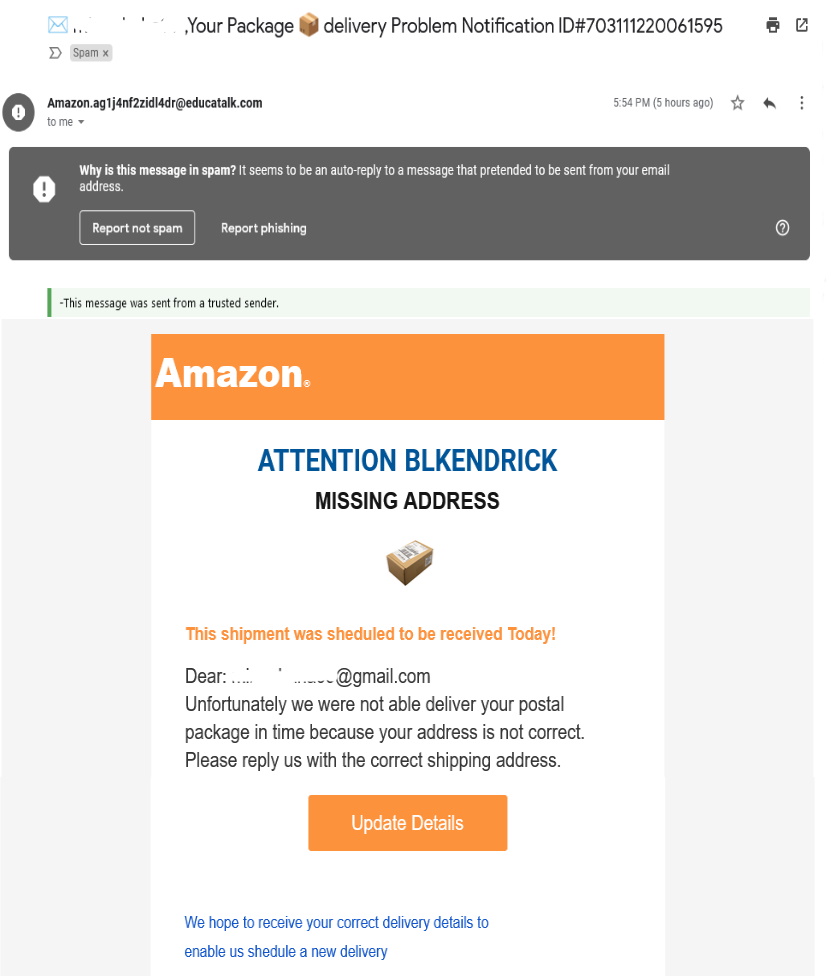
So, an inexperienced person faced with such an email would think, ‘oh wow, ok!’ Then ….. click. They get whisked off to some website that looks like the real deal so this person goes further by entering their personal information. And Spam malware has captured the information.

It will make it’s way to your friends, family, social media (SoMe) accounts, bank, and wherever personal information is entered, capturing information from one person’s contacts, and moving onto their contacts. It is said that it takes using “10K computers sending 10K emails each” to finish quickly. That’s a lot of infected computers, yes?
How to Identify Spam from Legit email?
Learning the what, where and why of Spam is a great first step towards helping yourself from becoming a victim. It’s also recommended that we approach our emails ‘ on the defensive‘. Keep doubt nearby when checking your email. Do not believe everything you see in your email or other social media (SoMe) accounts.
Let’s examine this email image, yes it’s from my own Spam file and note the RED underlines. I clicked on the little grey arrow next to my email name to OPEN this information box;
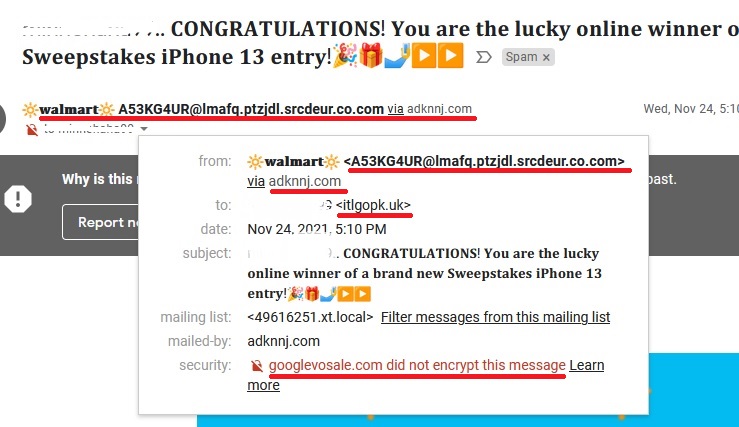
Fortunately, I don’t fall easily for such emails and it was in my Spam. Sometimes emails from family ends in the Spam folder especially if sending links that triggers the web browsers Spam algorithms. It gets annoying but I check. Back onto topic … did you notice the grey box and what it says?
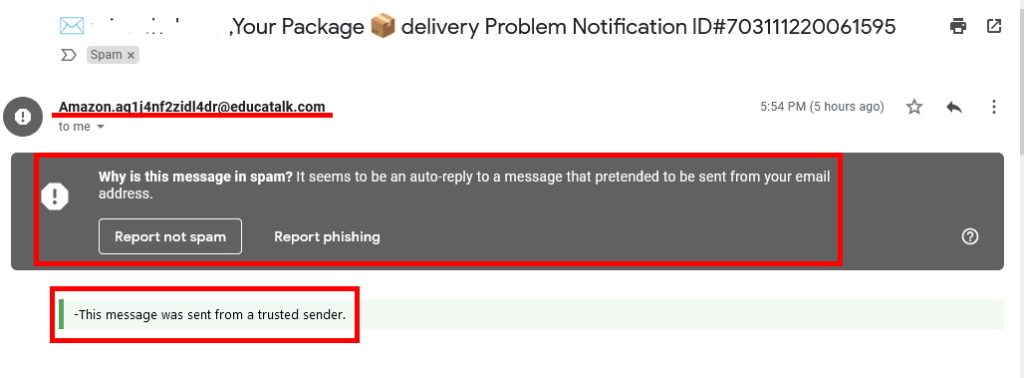
Well, if it was real, I don’t think it would have such a strange email address, right? Still not sure? let’s go check Amazon’s available information and email, and we have ;
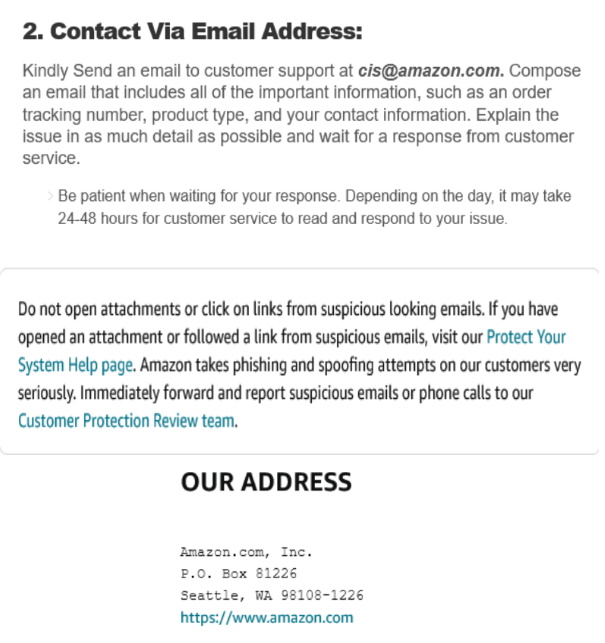
One other interesting sign of Spam emails was a surprise to me too, check it out on this image;
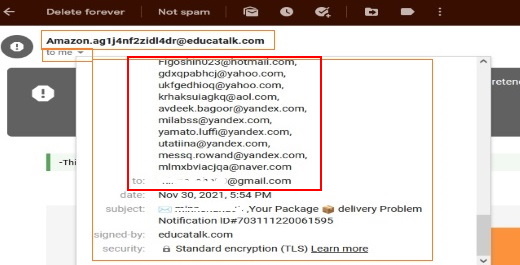
Wow! see all those addresses? and mine was scooped in there too. An interesting time to mention about another Spam practice. It’s ‘flooding‘ your email with Spam. This is to ‘hide a transaction’ done in your name.
So, if you’re getting ‘flooded‘ with higher than normal rate of Spam. Maybe it’s time to do a quick check on our credit card transactions? Change passwords or security numbers. Just a thought.
One last tip that I recently learned. Downloads. If you buy or make downloads, sometimes your Anti-Virus will notify you so you can easily toss it. Other times it may not get immediately caught so … you can use your Gmail Docs to open it.
Google claims a high rate of Spam capture. If you’re suspicious of a download, open it in your G Docs and see if there’s an alert. If there’s nothing then it’s safe to open on your own computer. We like to believe that our systems are protected but it’s not 100%. We got to do our own part and as mentioned earlier, let’s learn to be in ‘defensive‘ mode when checking our emails.
Learning in Motion
Further Learning Resources
8 Tips to Protect Your Computer From Viruses and Malware
5 safe ways to get back at spammers: a guide to wasting time
Your Guide to Starting a Career in Cybersecurity
I hope you found this article informative and gained some new insight. Please feel free to Share with others! and leave your comments. Use the ‘Ask a Question’ form to make a request on a topic of your own interest. I hope you visit again for more informative articles coming soon. Stay safe!
AIC|An Informal Cornr, all rights reserved. Ginsense writes articles on business, health, science, technology, society and enjoys advocating for independence, security and a better world for all of us.
